The most recent attempt to launder stolen UPbit hacked funds involves an array of well-known exchanges
-
Published
2020-05-15
-
Author
Clain Team
- Topics Binance Huobi Investigations OKex UPBit
- Share
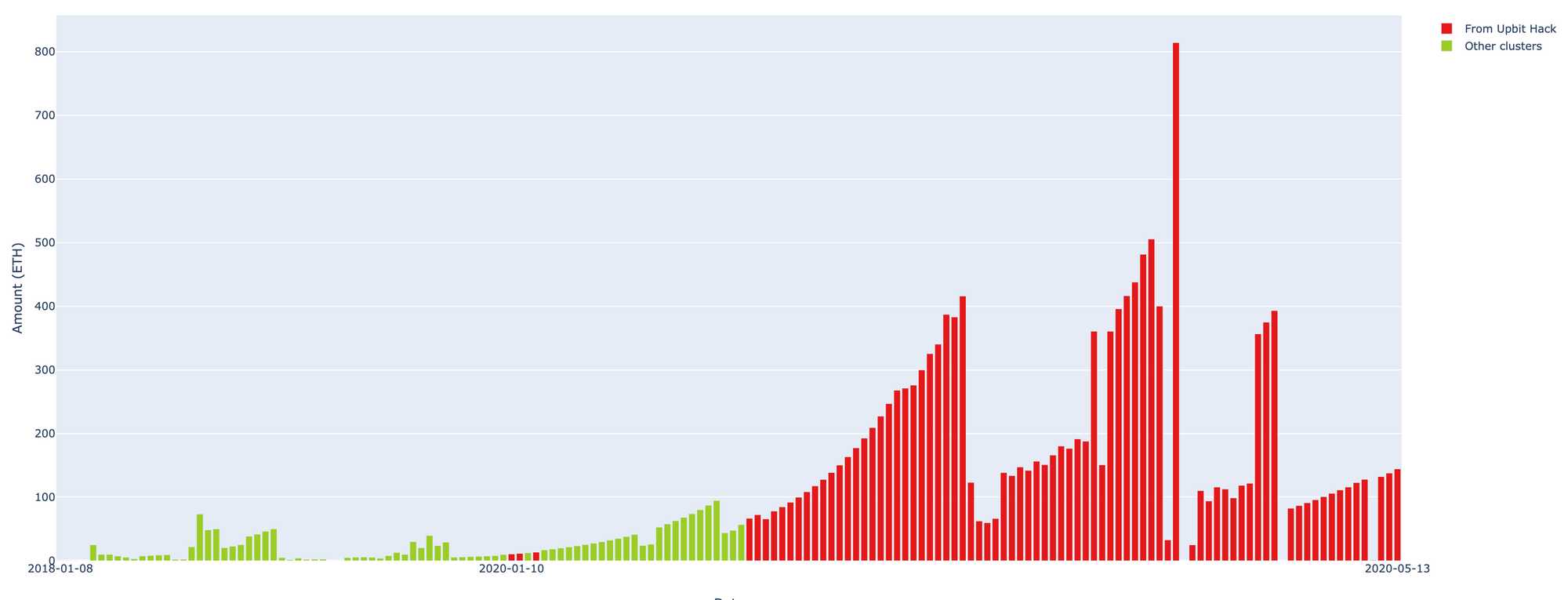
Upbit exchange was hacked on November 27, 2019 resulted in ETH 342 000 being stolen. Since then, more than ETH 236 000 was laundered through various crypto exchanges during the months of December and January, the rest has been sitting idle on hackers’ wallets until recently.
Few days ago, Clain was alerted that the stolen funds started moving again, and by May 15 an additional amount of ETH 70 000 were channeled.
Using its proprietary compliance and investigation platform, Clain has looked into the case to detect specifically where the stolen funds were moving to.
Below is a funds flow chart of the hacker wallet comprised of thousands of ETH addresses used to launder:
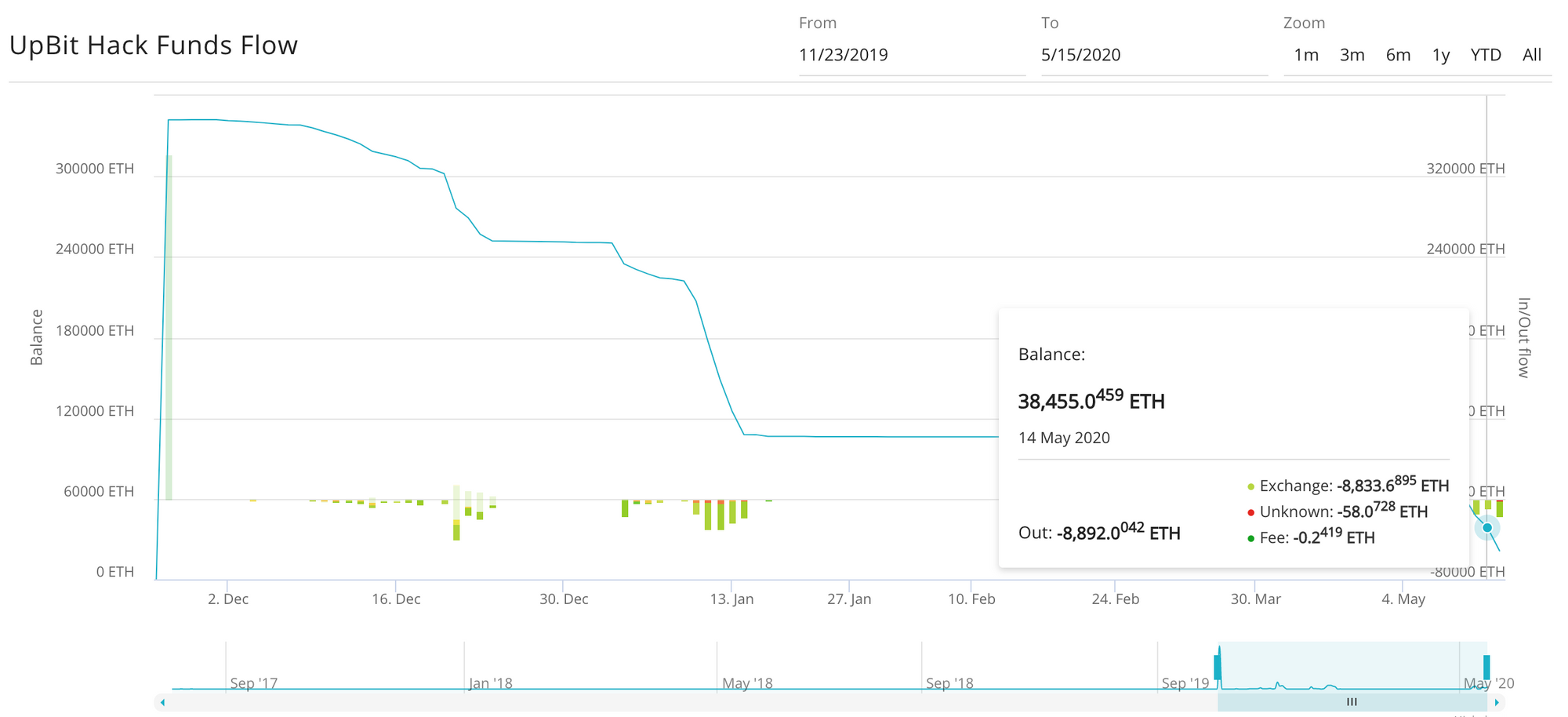
We have detected that the most recent attempt to launder the stolen funds involved a number of prominent, well-known exchanges. Until now, over 85% of the funds are successfully defined by the Clain platform, to be flowing into exchanges such as Binance, Huobi and OKex.
In below graph you see the timeframe with cumulative ETH amounts rushing to major exchanges:
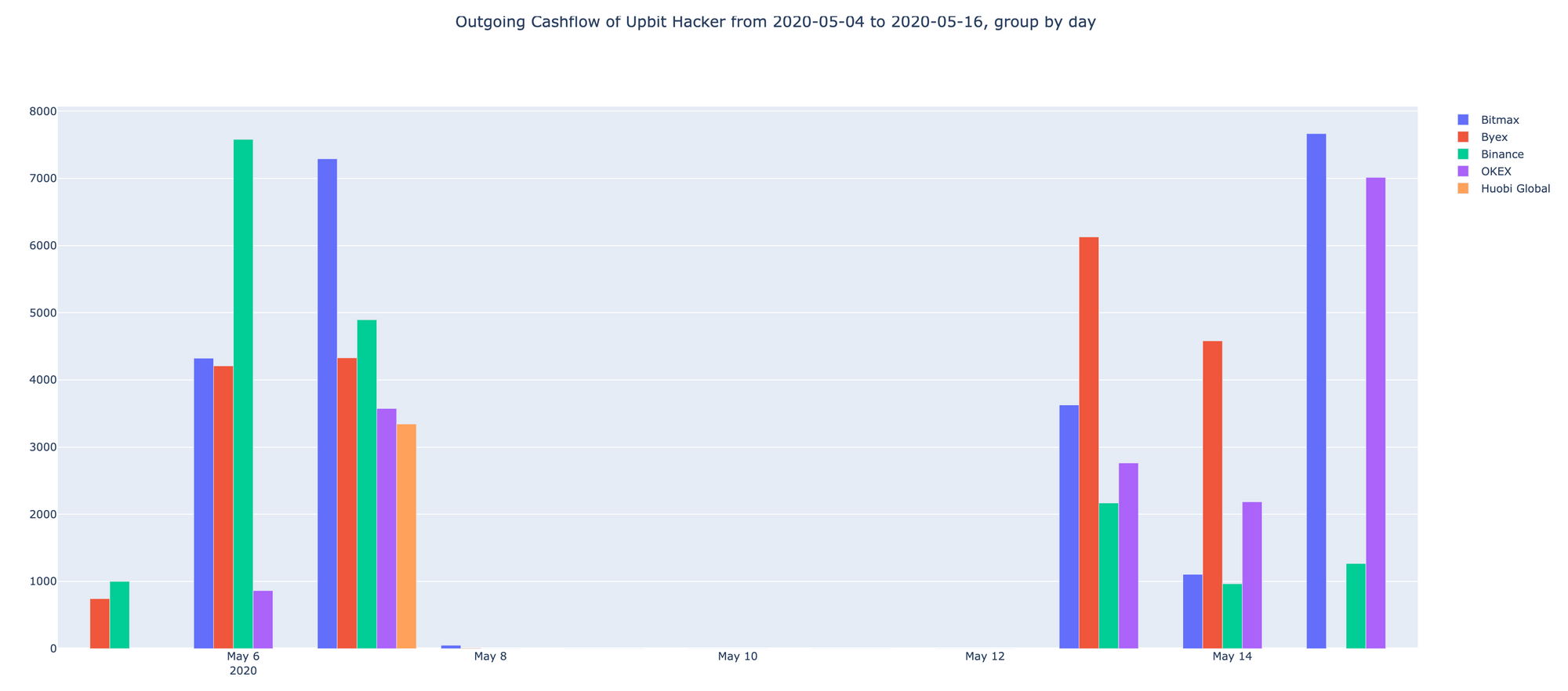
Analyzing further hacker-controlled wallets we have detected that it was trying to obfuscate stolen funds via Tokenlon wallet exchanging it to USDT and other stable coins but failed as it mixed laundered money with illicit sources.
Here is a complete view of the incoming and outgoing flows of Upbit Hacker wallet since May 1 to May 15:
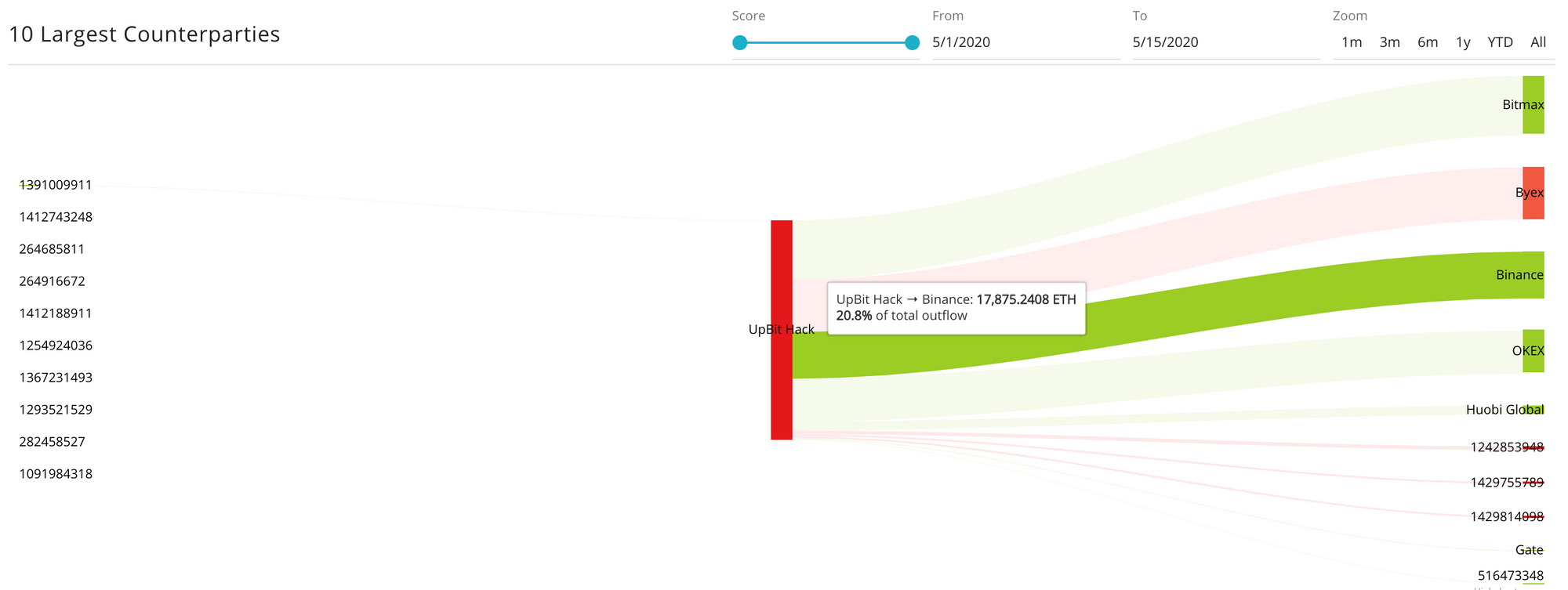
The entire distribution of May launder funds along with the recipient names can be observed here:
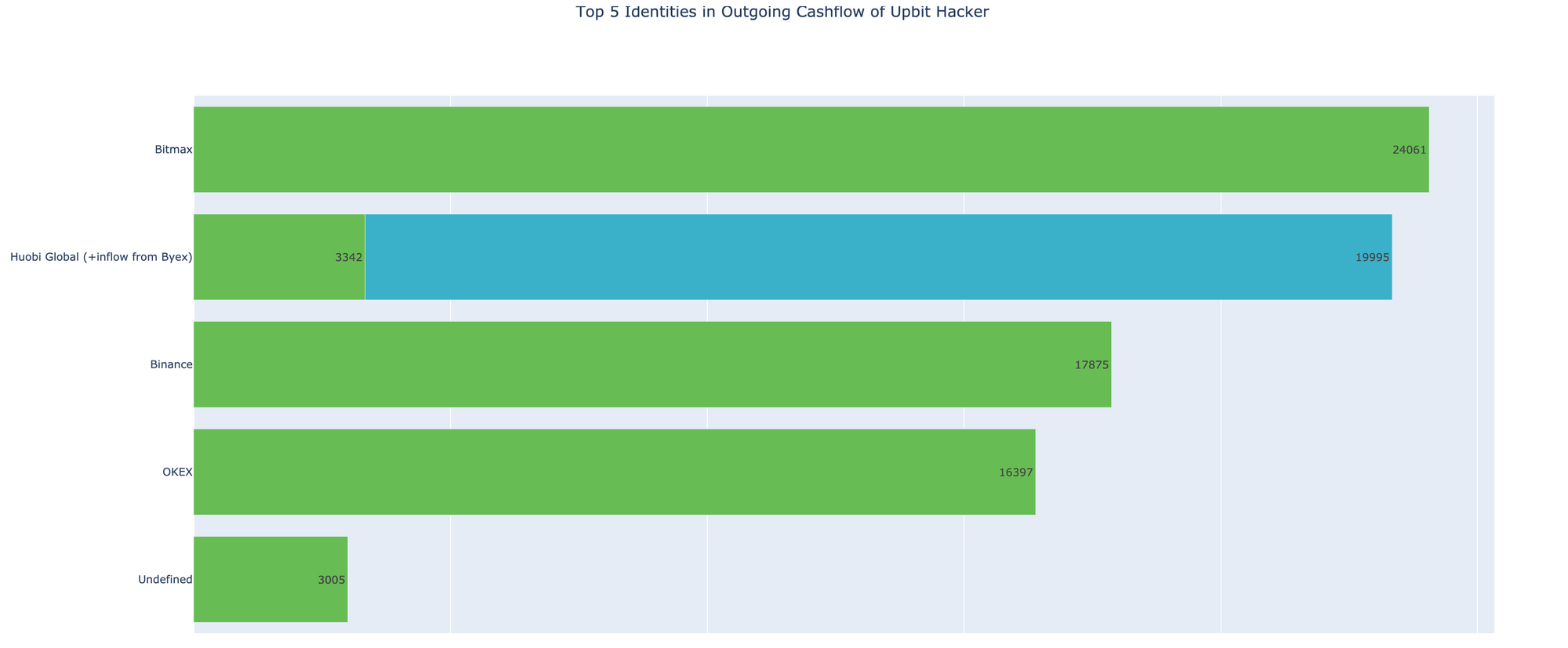
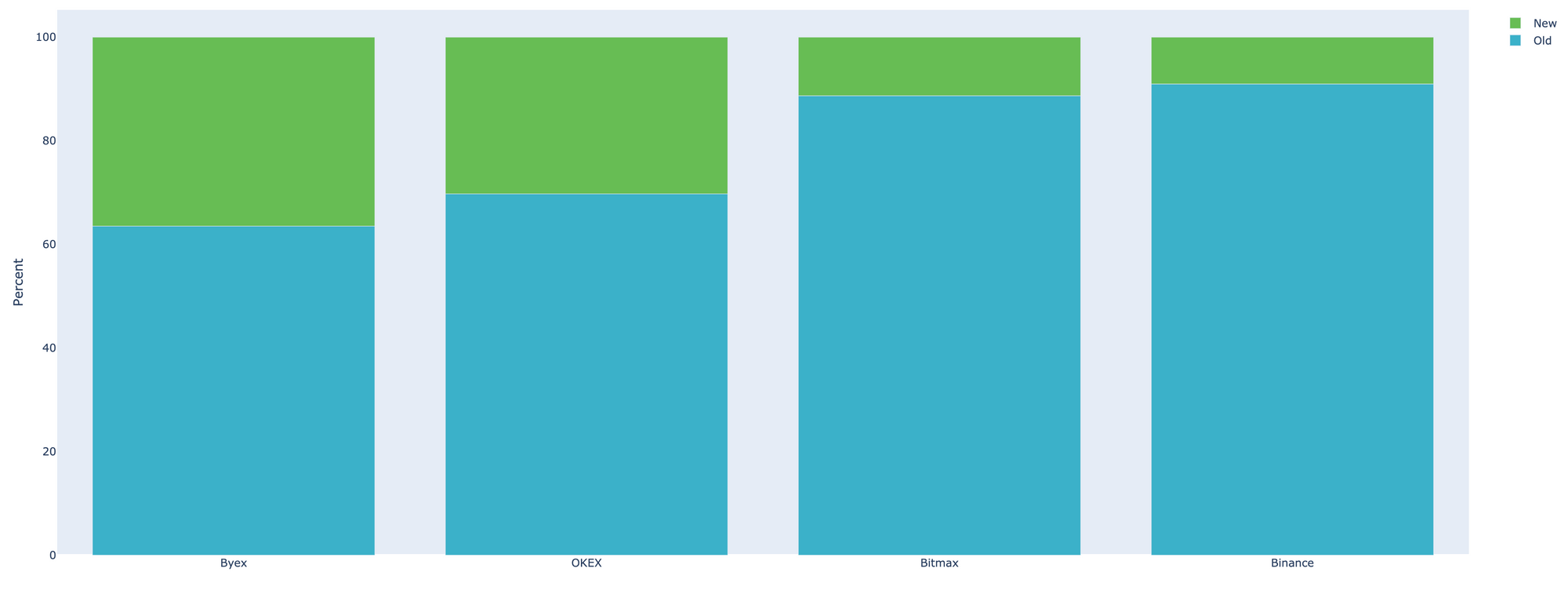
Interesting fact though to note is that, as soon as the crypto exchanges became largely aware of the influx of Upbit tinted money, some have announced of freezing accounts to cease the launder. However, looking further into deposit addresses the hacker used to send money to, we noted that there is only a small fraction of newly created addresses, the majority is the old ones used previously.
This fact alone should imply that the previously used addresses have not been blocked by exchanges, but rather allowed hackers to repeatedly exploit old accounts over and over again.
Below is the ratio of newly created vs old addresses on the major exchanges affected:
Byex is among names that was affected by outright launder. The officials have hurried to deny that the destination of hackers’ funds was in fact their exchange addresses (snapshot of Byex response included). But we can assure that the aforementioned addresses do belong to Byex and are frankly surprised by the official false statement.
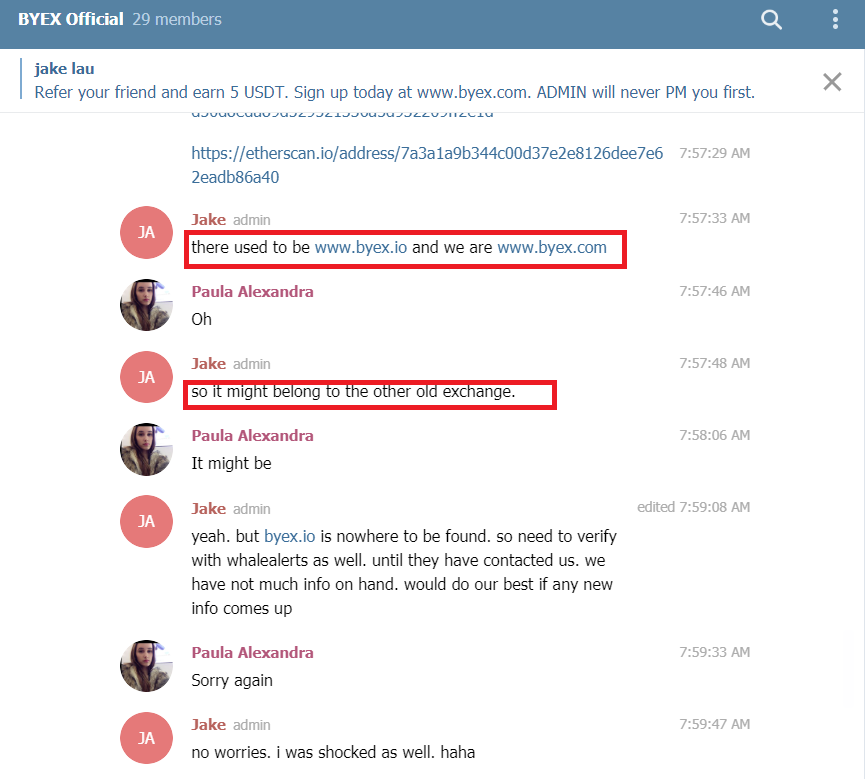
To us though it remains very clear that given abnormal volume of incoming funds, Byex should have been alerted and taken the appropriate measures to counteract the attempts. But nothing seems to be done as the inflow of stolen money was neatly balanced with respectively laundered outflow.
Here is the funds flow chart of Byex exchange:
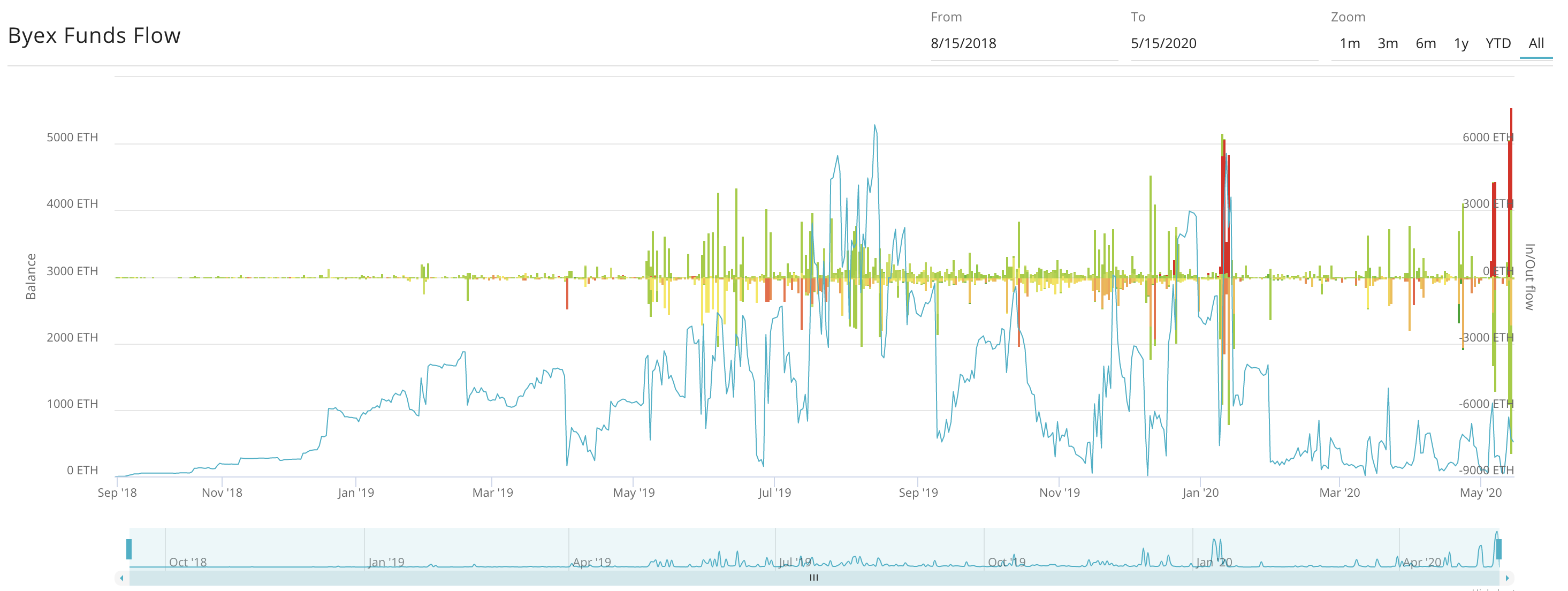
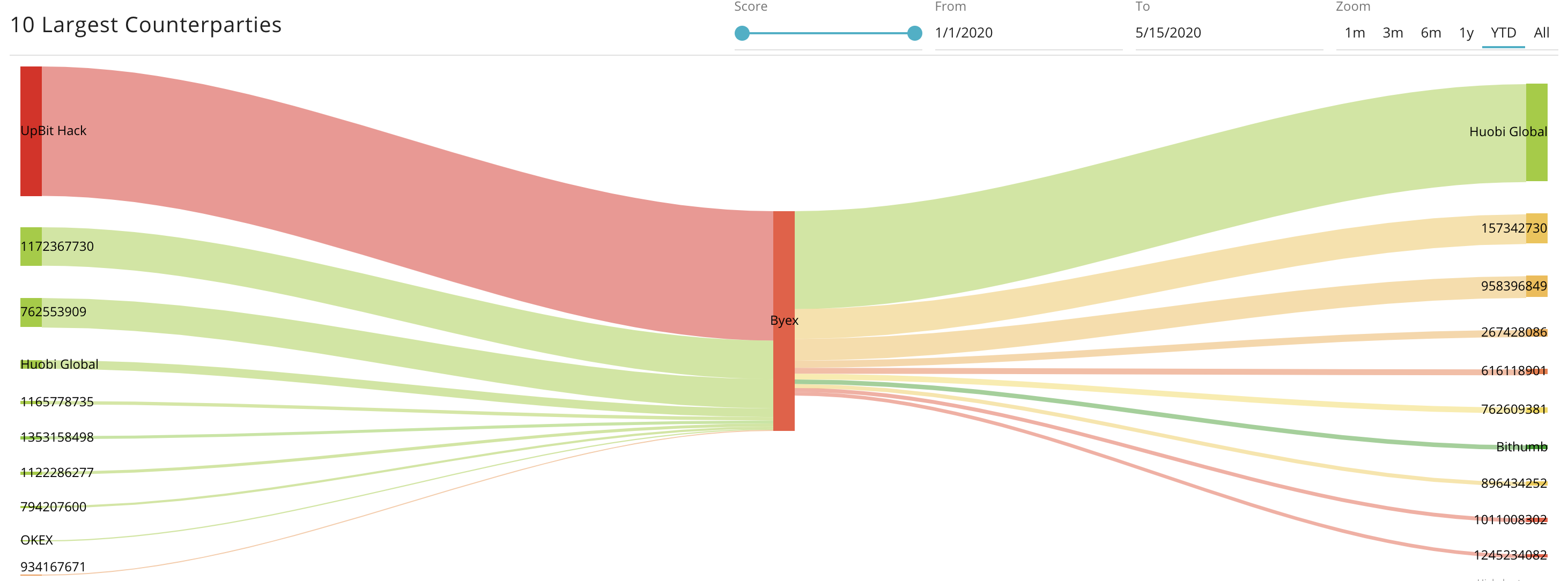
There is evidence to assume that Byex exchange was primarily used to obfuscate funds prior to sending it further to Huobi.
Relatively the same amount of ETH that first landed on Byex was next headed to Huobi exchange (as illustrated below)
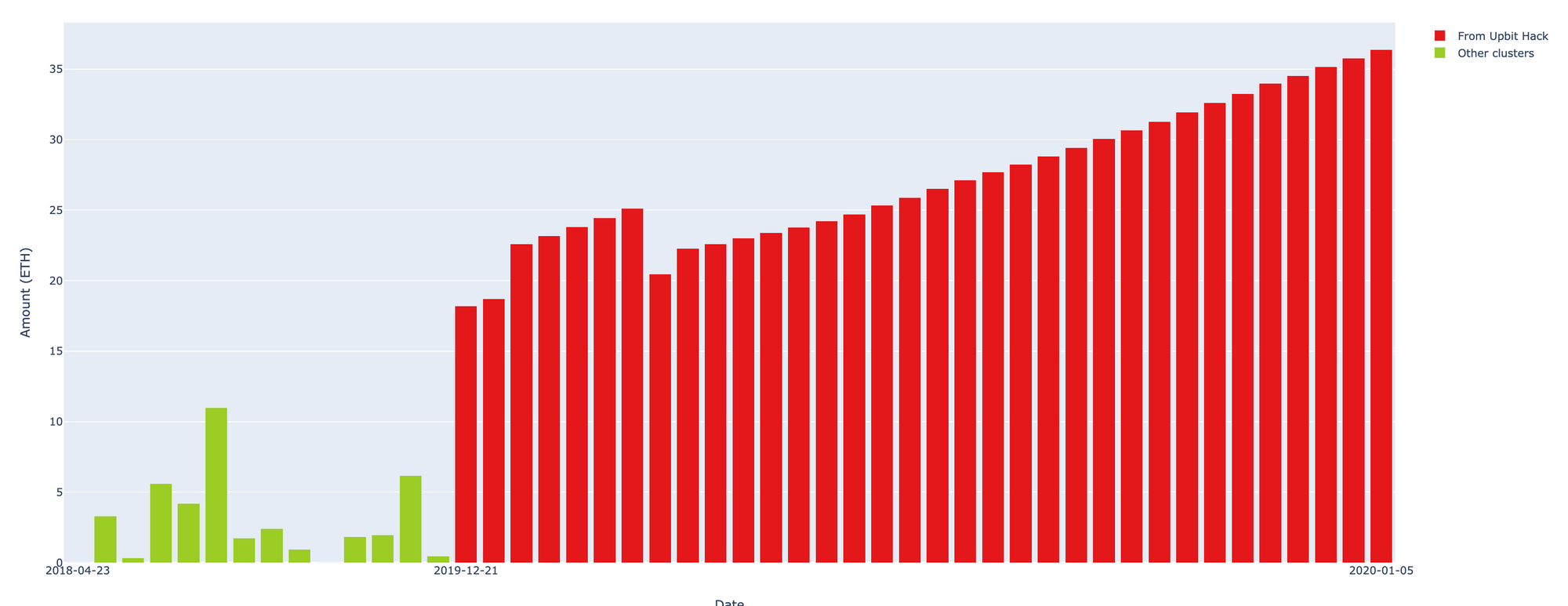
The officials of Binance exchange have announced that they blocked transactions of Upbit hacker. However, the data reveals that deposits addresses the hacker used was in fact active long time ago. The addresses systematically accepted the stolen funds and have not been blocked up until now.
Here is the chart of the example of such flow:
Similar announcements were followed by OKex and the illustration confirms the activity of address for a longer period.
Below is the aggregate table of recipients of Upbit stolen funds with identified amounts for the entire period: