-
Published
2020-09-29
-
Author
Clain Team
- Topics Binance BitMix Investigations
- Share
Recently our team stumbled across the article on “Ransomware: Prevention, Investigation and Bitcoin Funds Recovery” written by CipherBlade - a blockchain investigation agency. In addition to good information regarding the need for good security policies and having an effective blockchain analytic partner, the article used the CWT Ransomware attack as a case study.
The case study discusses the use of a Chainalysis tool by CipherBlade to conduct the investigation, which is currently considered a high quality standard of tools for blockchain analysis.
As a provider of blockchain analytic services for investigation and compliance, we are always in the routine of analyzing prominent hacks and we have been following the CWT ransom with care and conducted internal investigation using own tools a while ago.
After reading the CipherBlade post, we found some discrepancies in the report that we believe addresses the reality that current, highly regarded blockchain analytic companies may have many tools at their disposal, but the complexity of this work requires resources that must allow these companies to look “deeper” into the blockchain. Our approach has always been to utilize speed and the best designed tools with our vast background of working in this space to provide the most comprehensive view of activity on the blockchain for over 90% of all cryptoassets.
Unlike CipherBlade’s main takeaway which declared that all of the extorted funds were syphoned off into four different exchanges, we found that a big chunk of that money actually headed to what’s known as a “mixing service”.
This fact alone largely changes the landscape of parties involved in the schema and if we put our own findings into the same graph, the changes would look as follows:
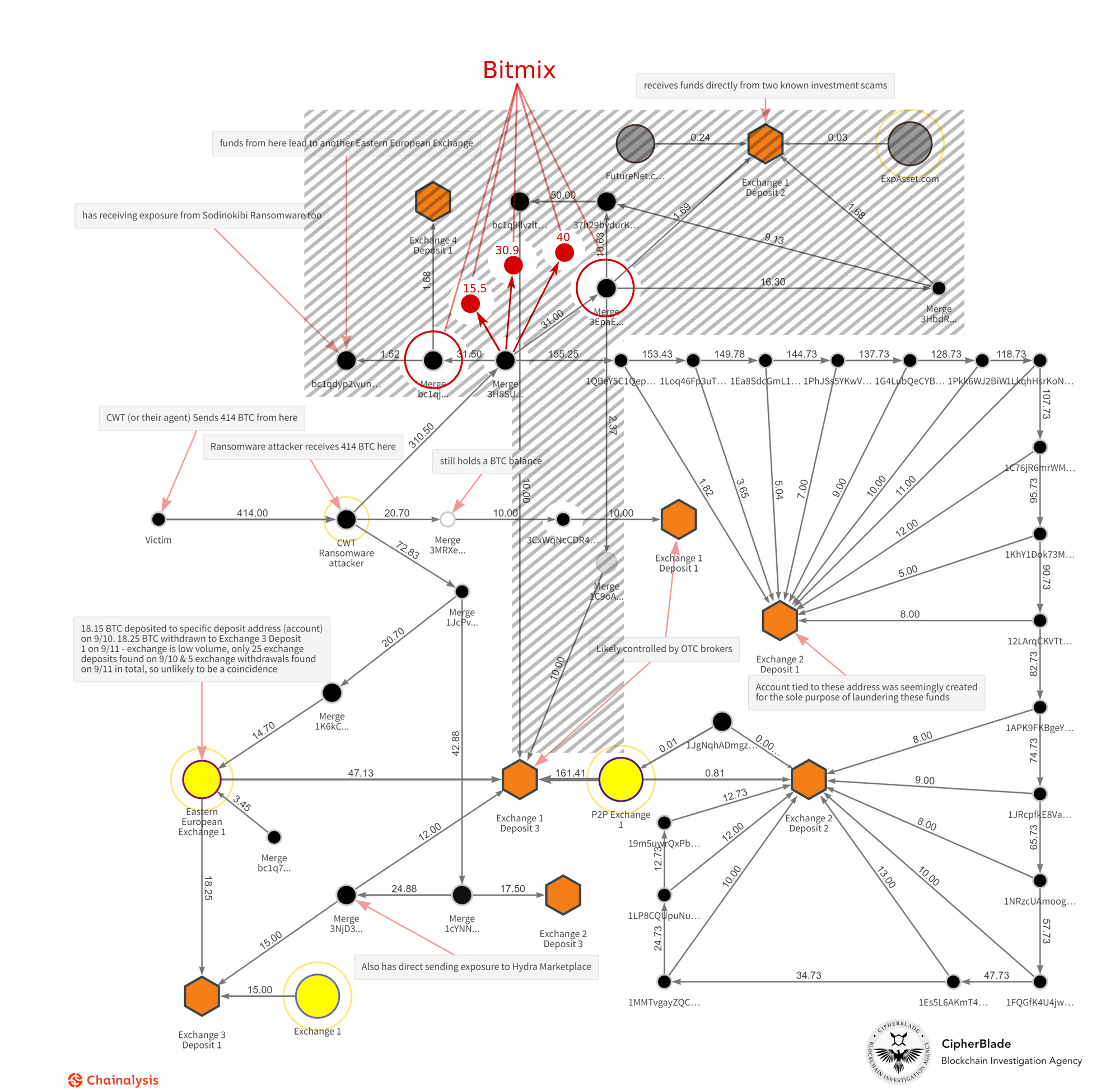
CWT Ransom through Clain’s vision
Let me walk you through the analysis of this hack that we did here at Clain.
Attackers received 414 BTC from CWT company on July 28, 2020. Following next 5 days these funds were moving to two primary destinations:
- Binance exchange - 173 BTC (42%)
- BitMix mixer - 149 BTC (36%)
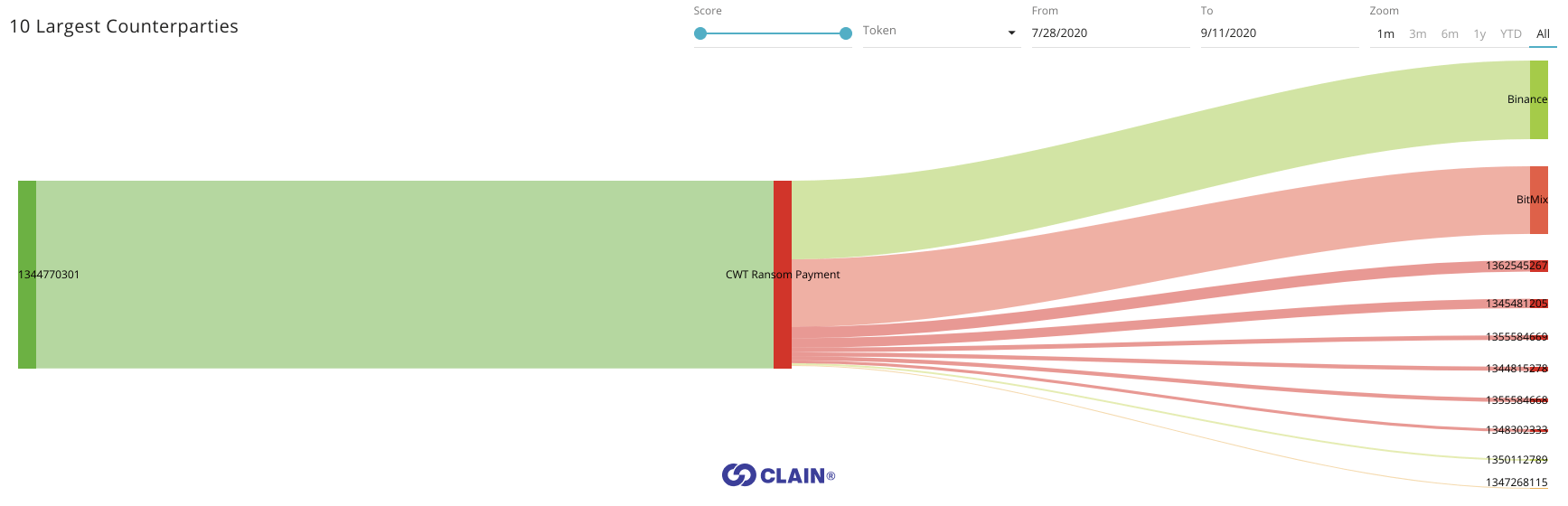
Binance
Sending extorted bitcoin to Binance was a bold action to say least, and the hackers did not take any precautions to obfuscate criminal funds before sending the money directly to the exchange. It was done blindly by executing a sequence of peeling transactions targeting Binance and this was correctly spotted by CipherBlade.
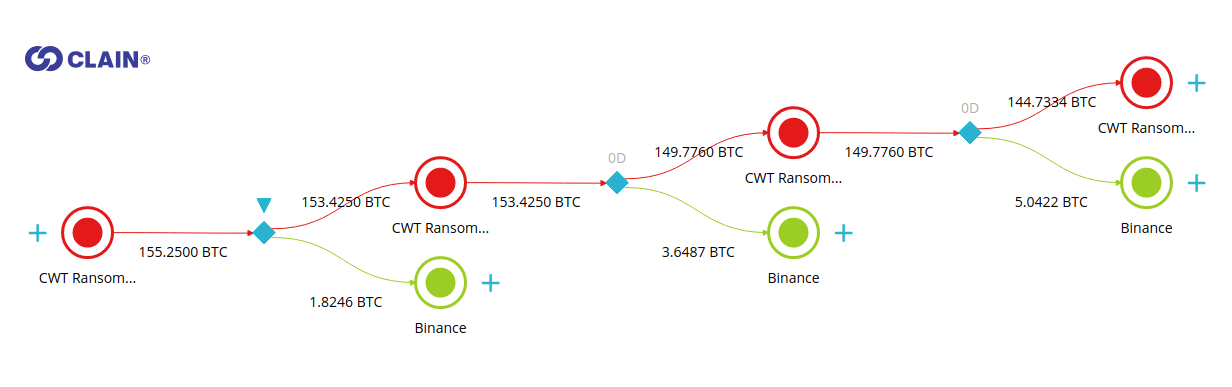
A major way that we address these crimes is to examine how the “clustering” of bitcoin addresses can expose the actual crime and laundering being conducted. Peeling chain is a set of heuristics we use for our unique process of clustering bitcoin addresses in the transactions that have one input and two output addresses and where one of the output addresses is the recipient of the funds, and the second address is a change address of a sender. While analyzing the flow to Binance, we found that several of its deposit addresses had been receiving money multiple times:
- 172GfiBzkfR7BApTa4MeP8g7kEtZXXQdC1 - 82.7 BTC (total of 8 transactions)
- 1BmHod3JFGmBvomkqDA8SMdEYnSYJnpaiE - 72.5 BTC (total of 10 transactions)
The fact that extorted money was accumulated in such a quantity and through a large number of sequential transactions at Binance raised plenty of questions and leads us to believe that the owners of those accounts had successfully passed KYC or bought a verified account on DarkMarkets. Otherwise they would need at least 40+ days for withdrawals as the Binance exchange imposes 2 BTC daily limit restriction for all unverified crypto withdrawals.
BitMix
Unlike CipherBlade’s findings suggest, we believe that a significant chunk of extorted money went to the BitMix mixer. BitMix is an advanced mixer that largely complicates the detection of its deposit addresses and breaks the ties between money sent to and money received from this mixer.
Investigators working in the blockchain analytic space need to use the proper tools and resources that over time have been shown to detect the real exposure or it’s relatively easy to get trapped into an incomplete analysis. BitMix transactions, in fact, look very much like Binance peeling transactions shown earlier, with one major distinction – the money sent there cannot be tracked easily down.
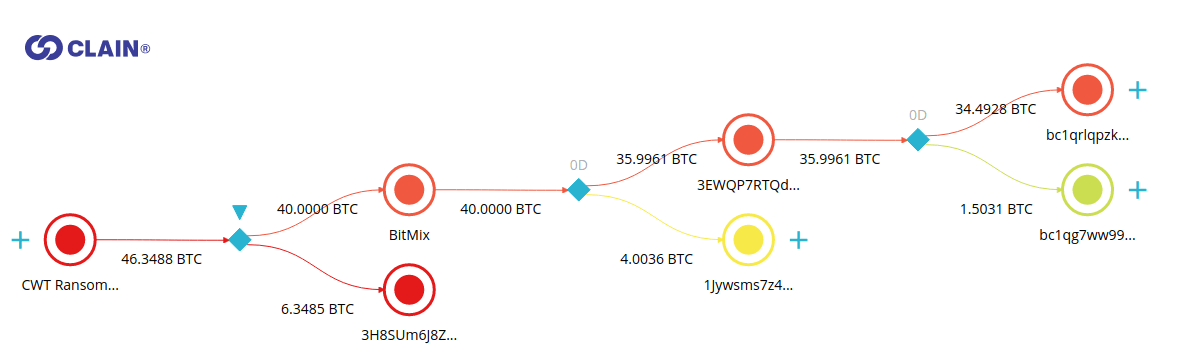
How do we know that it went to BitMix?
Clain uses the pattern detection algorithms to track the behavior of a large number of mixers where BitMix is one of those services.
The attributes of BitMix transactions notably differ from the attributes of transactions that the attacker was using when sending the money to Binance. We also noted that other BitMix transactions, unrelated to the CWT ransom, utilized the similar attributes.
Unlike Binance example, the output amounts in BitMix transactions are not round numbers, which is a typical method of break peel chain heuristic.
Moreover, BitMix was spotted in being a laundering tool for other well-known extortions, such as NetWalker (800 BTC in total) where the proceeds of which exceeded all other flows in the mixer.
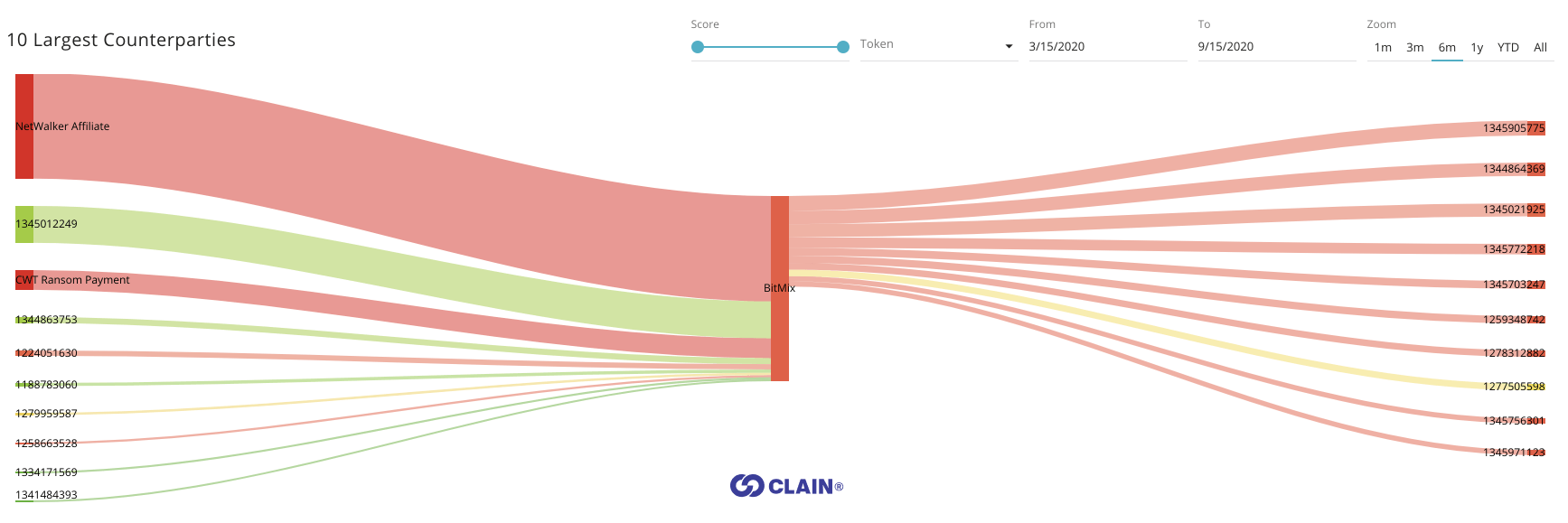
In the report, there is no mention of the mixing services to be in play, which Clain thinks is a significant omission of the analysis and leads to an incomplete conclusion.
Clain is a blockchain analytics company that grew out of the founders’ ambition to create the fastest, more comprehensive tools and resources to uncover and utilize the transparency of the blockchain. We believe that blockchain’s transparency allows for a fuller picture of the activities occurring on it, whether by good or bad actors. We’ve built tools and resources that are helping exchanges, businesses and investigators worldwide to address compliance and criminal activities on the blockchain.
Clain is the only blockchain analytic company that provides real-time analysis with a proprietary scoring system that identifies criminal activity and bad actors faster and more completely than any other blockchain analytics company.
If your company, exchange or investigators need the most complete blockchain analytic solution available worldwide, contact us. As we’ve detailed in this article, we consider that our blockchain analytics provides the most complete solution available on the market today.