-
Published
2020-03-27
-
Author
Clain Team
- Topics Investigations Huobi
- Share
PlusToken Ponzi
The first appearance of PlusToken dates back to beginning of 2018. In the course of its multi-year existence, more than 480 000 BTC managed to pass through this Ponzi, while more than 195 000 BTC were effectively stolen by the originators.
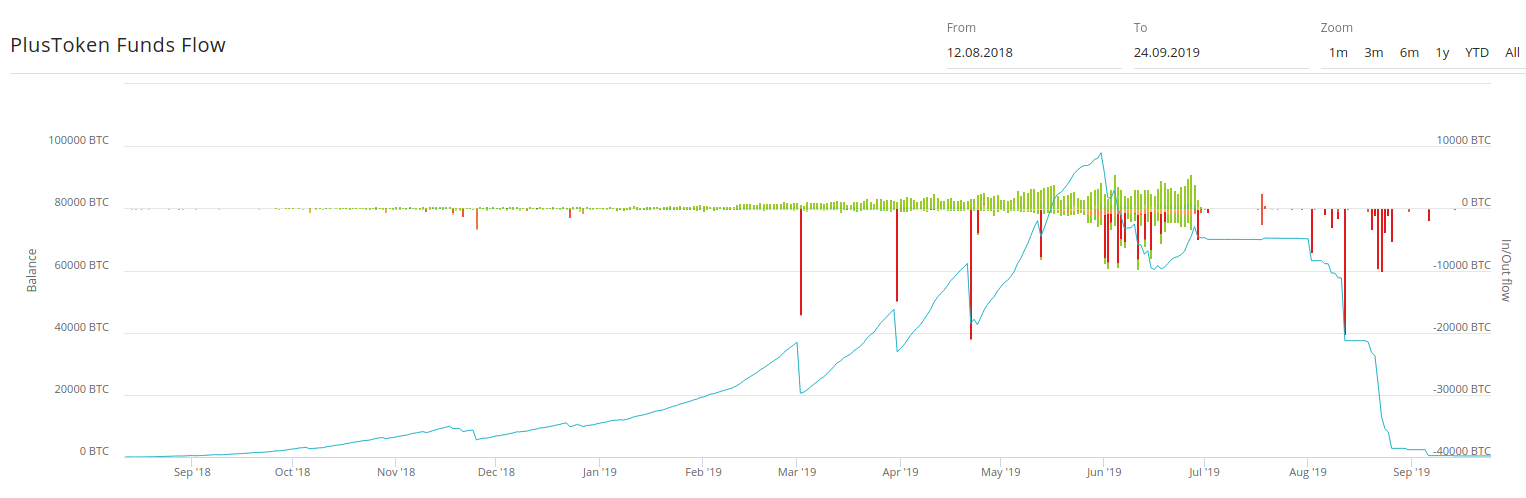
Clain was able to get into interesting details of PlusToken Saga using its proprietary investigation and analytics platform.
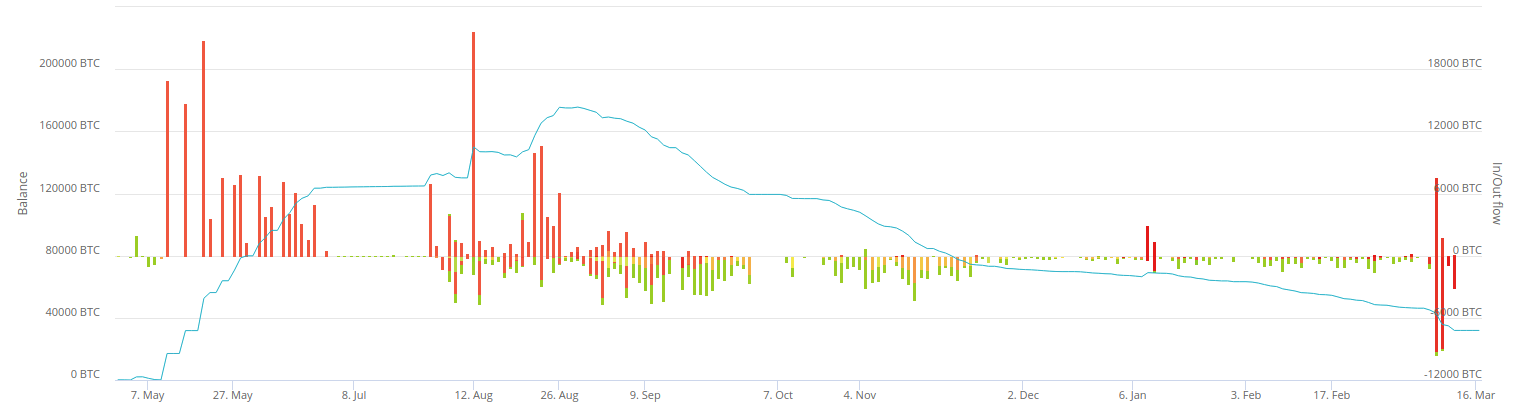
The scale of the Ponzi is well illustrated in the above chart that shows inflow and outflow funds of PlusToken (vertical bars) and corresponding overall balance of BTC within time (blue line).
The pattern of the flows immediately suggests the following takeaways:
- Clients steadily and consistently transferred moneys up until July 2019
- The inflow of incoming funds resembled the exponential growth which is typical for any Ponzi to secure the uninterrupted withdrawals of existing clients.
- The collapse of the service was likely staged in advance – there have been huge one-off withdrawals of funds by originators since the start of 2019. The funds landed in personal wallets of the originators to be further accumulated and stood ready to be laundered after July 2019.
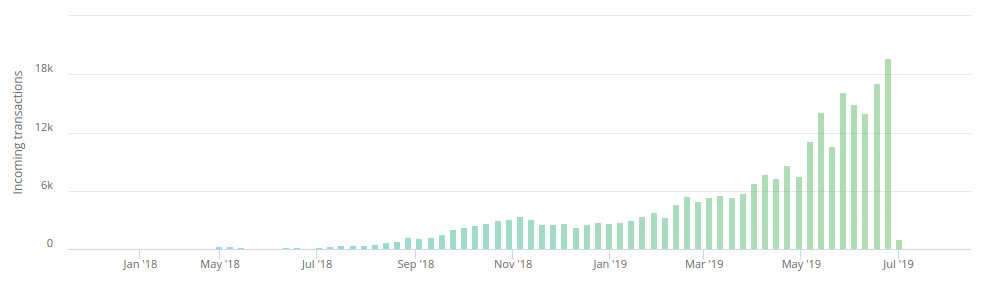
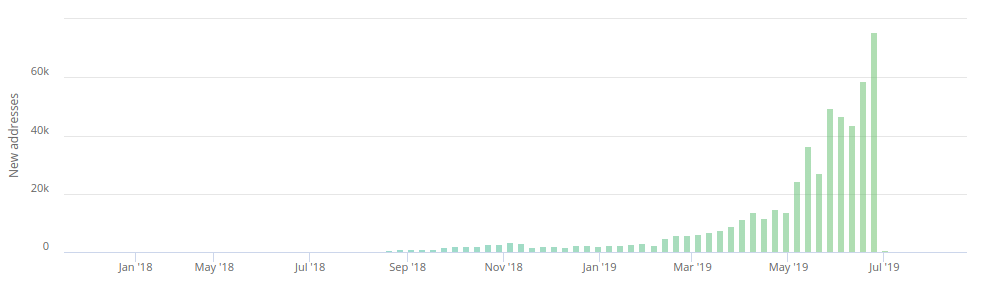
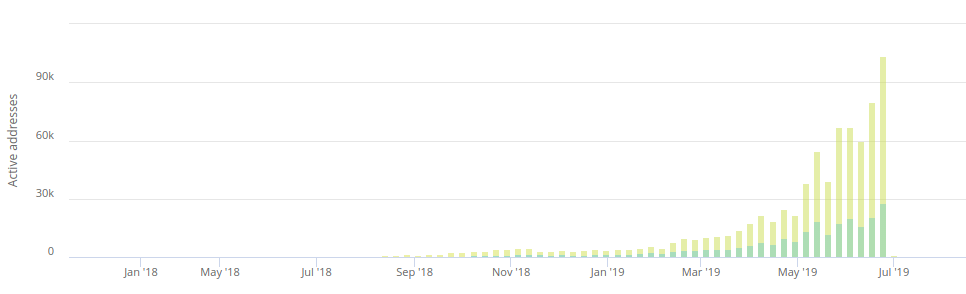
The charts above is just an extra example illustrating the exponential growth in PlustToken activity, which was abruptly halted in July 2019.
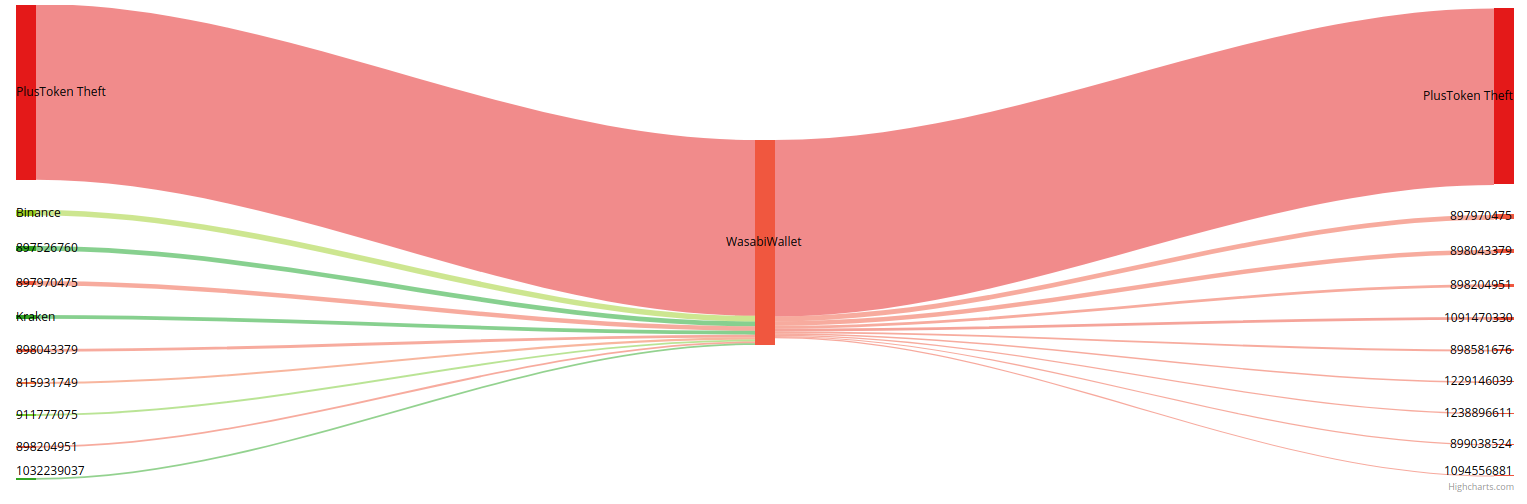
Top-10 counterparties of PlusToken based on in- and outflows BTC:
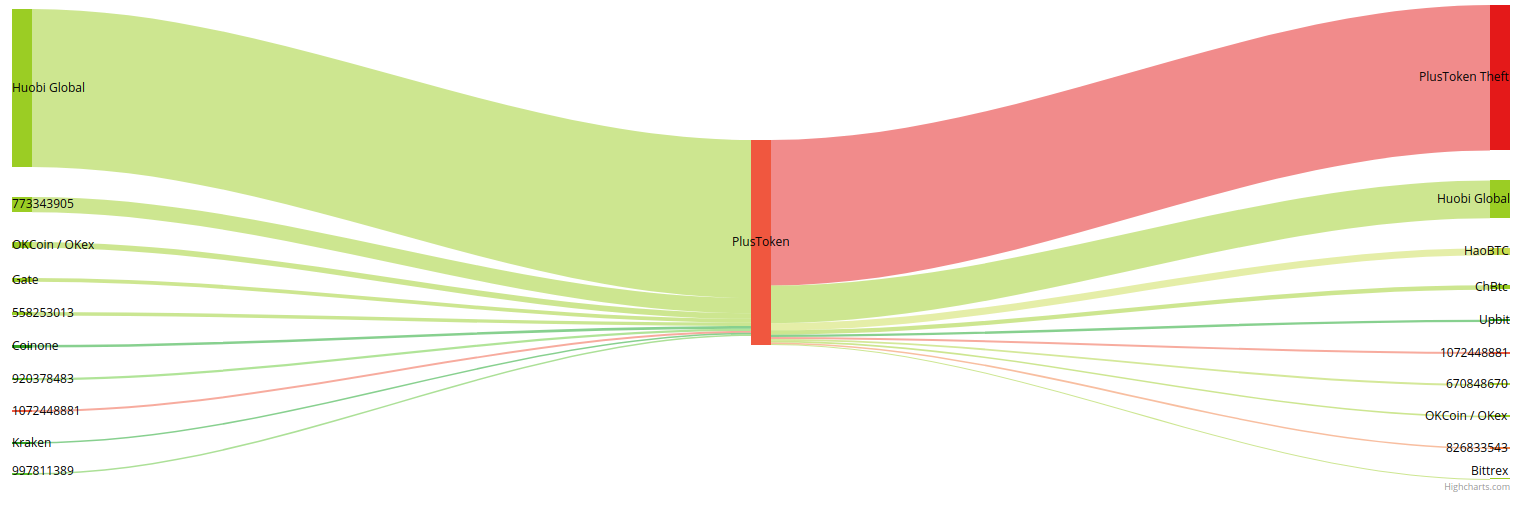
Excluding the actual theft of the funds from PlusToken, the notable counterparty PlusToken was dealing with is Huobi Global Exchange. Top-5 in relative terms looks as follows:
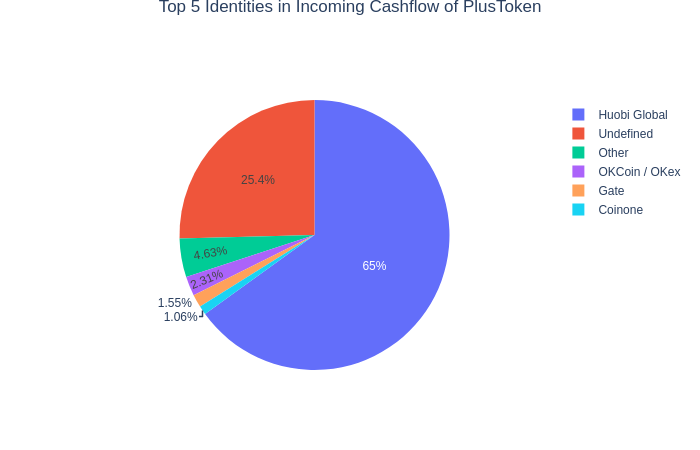
Apart from Huobi, the remaining part of the funds arrived from OkCoin, Gate, Coinone and some others.
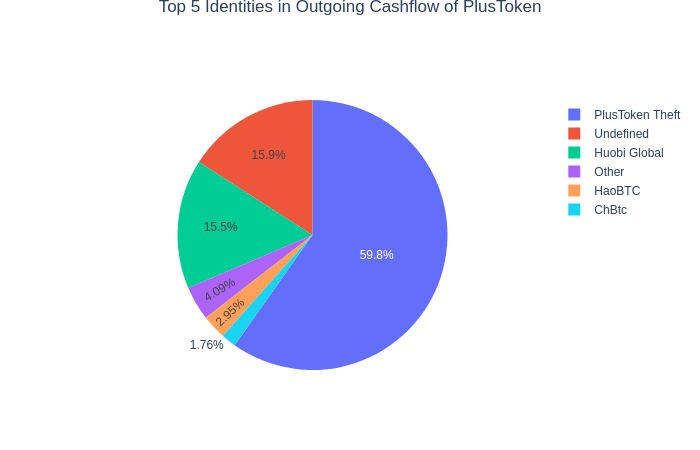
As regards to the outflows, the largest chunk of the funds (around 60%) went to thefts’ personal wallets, the rest of withdrawals headed to Huobi, HaoBTC, ChBTC and others.
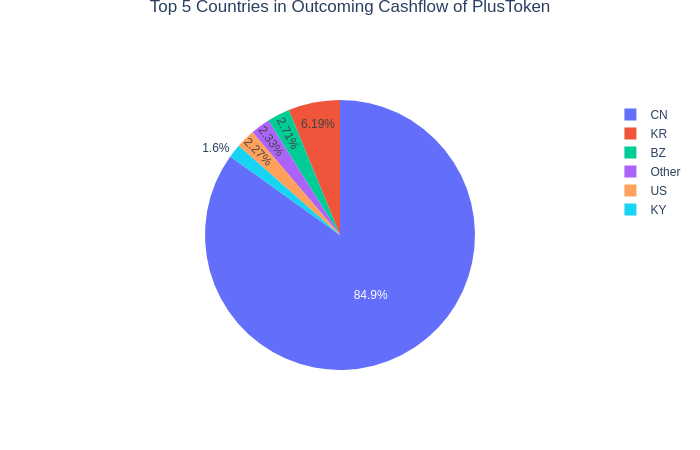
The geography of the flows is as follows:

PlusToken Theft
We aggregated all the addresses originators used to appropriate funds from PlusToken and put them into a cluster to analyze further. It allowed us to look at the capital flows of the stolen funds at more abstract level.
The chart suggests than the stolen funds were accumulated until September 2019. From August, they started to move gradually to exchanges using various schemas to break up a direct exposure to the illicit source.
CoinJoin-like
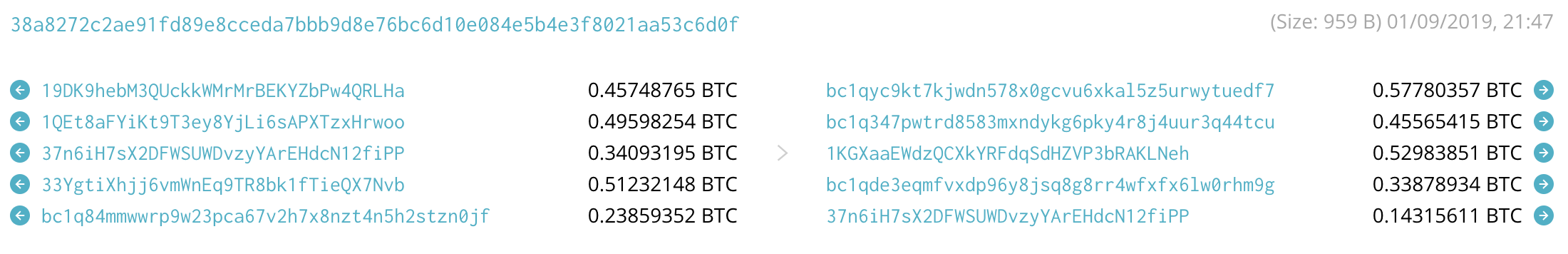
Fraudsters employed CoinJoin-like transactions to obfuscate funds. The part of the exercise included creation of transactions with multiple input and output addresses having different types (such as “1”, “3”, “bc”) to stiffen the efforts of tracing the genuine source of the stolen funds. This type of transactions should have mistakenly indicated that there were several independent parties involved, but in reality, all these belonged to the same party. The example of such a transaction is here (38a8272c2ae91fd89e8....):
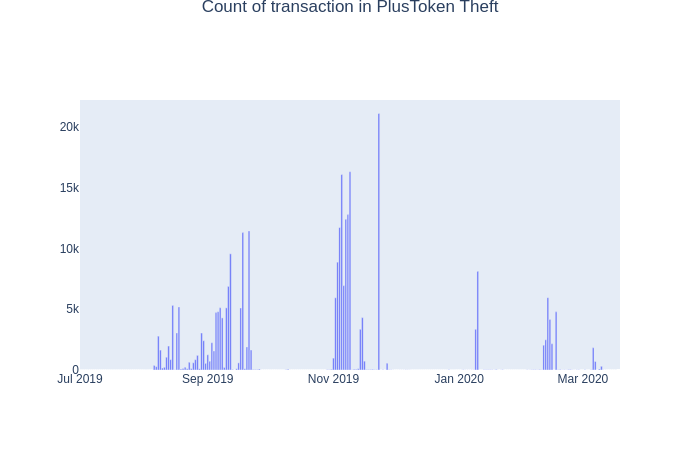
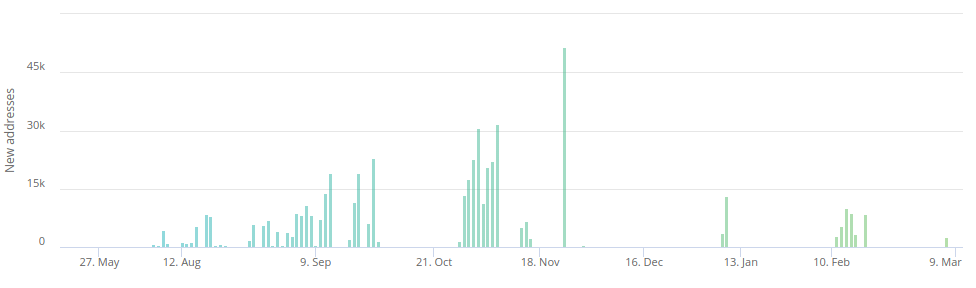
Transactions were forming a long chain of consecutive transfers that vastly expanded the cluster. The spikes in transaction count indicates the timeframe when the fraudsters were particularly active. For example, in November 2019 more than 20K transactions were algorithmically created just in one single day. Manipulations with consecutive transfers significantly complicated the traceability of the funds by having a myriad of addresses to go through. In the next sections, Clain has visualized the chain of those transfers to let readers comprehend the scale of the laundering mechanics. As result of these generated transactions, the theft cluster of PlusToken has grown up to 500K addresses.
WasabiWallet
WasabiWallet is the service that allows to create CoinJoin transactions, which is very much loved by criminals seeking to launder money. One of the prominent cases involving Wasabi was a hack of Dragonex exchange where more than 25 000 BTC leaked through this service. It is quite an effective tool to handle a daily flow of 100-150 BTC, but the effectiveness drastically falls short when a larger amount is being sent through as the funds get mixed up among the same user but not among a pool of independent participants as required (Read our post on Binance Hack and Chipmixer for more details). The below chart illustrates how flows from the PlusToken fraudsters disrupted the volume of operations of WasabiWallet during the time of the active lauder.
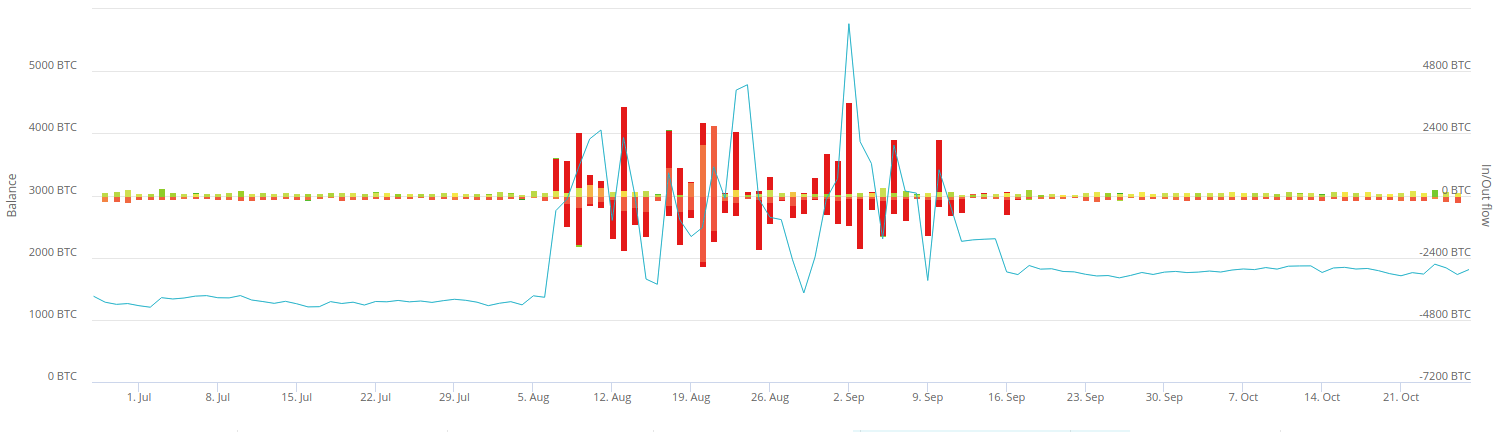
It is safe to say that the originators of the PlusToken theft were in hurry to move funds via Wasabi and avoided making a long chain of CoinJoin transactions. Surprisingly, the laundered transactions out of Wasabi were eventually aggregated with yet-to-be-laundered money having direct exposure to criminal source, which made whole previous laundering efforts absolutely pointless.
Below is the example how PlusToken theft dominated the entire Wasabi turnover comparing to other parties.
Visualizing the flow of the stolen funds
We have visualized the graph of the money flow within PlusToken Theft cluster to show readers how the laundering schema looks.
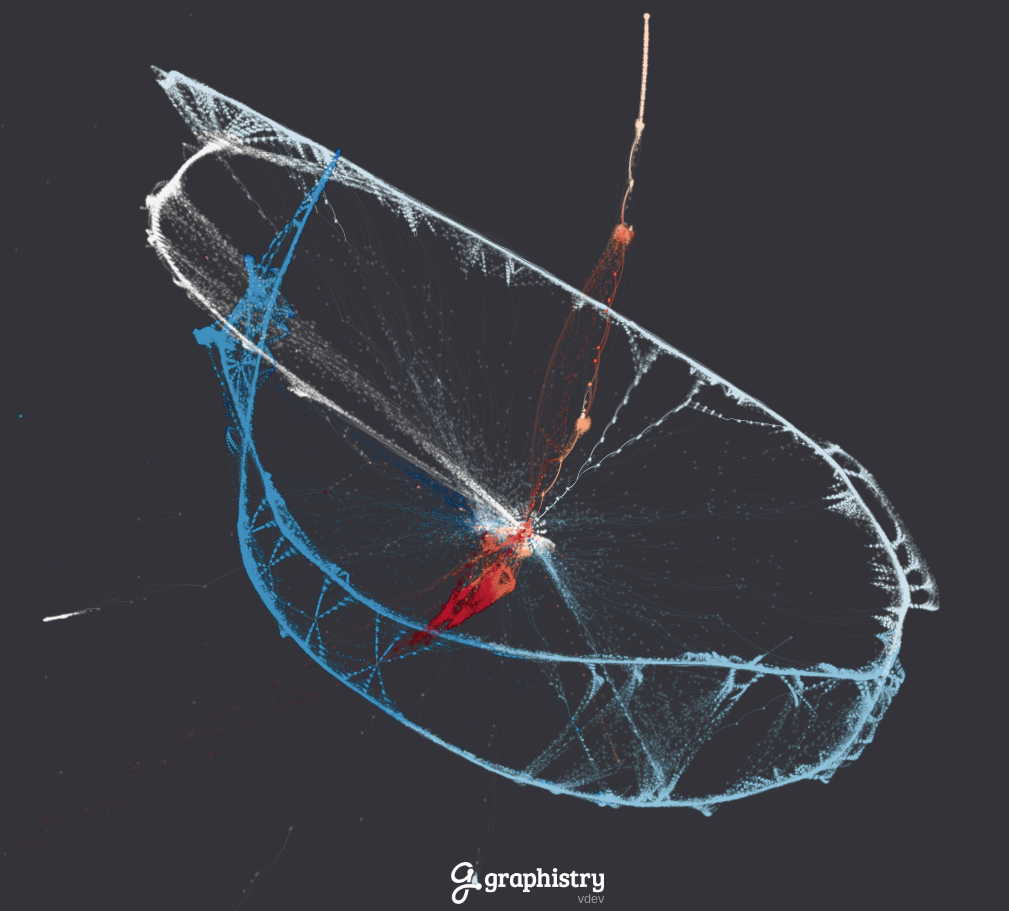
The first figure is the movement of funds for the period between August and October 2019. The color represents the age of transactions: redish – earlier period, blueish – later period. Nodes are the combination of input and output addresses within transaction.
We noted few interesting patterns there. First, the thick and long edges correspond to those famous CoinJoin-like transactions meant to obfuscate the original sources. Despite its huge presence on graph, the graph’s layout handles it nicely by making it easy to spot by a human eye.
Taking a closed-up look at the chains, one would be mesmerized by the number of addresses and transactions involved there. Focusing on a single transaction to trace back the funds will not be possible there. Yet, having a broader look at the intertwined chains appears to be easier to detect.

The bright red spot in the center of the graph is WasabiWallet cluster of addresses. It is the epicenter of the laundering scheme, the connections of different colors suggest that it was used for the entire laundering period between August and October. The less obvious red spot to the left is the Huobi exchange cluster, where fraudsters allocated a great deal of their proceeds after channeling through WasabiWallet.

To conclude, we have visualized the way how funds were appropriated from PlusToken to land into the fraudsters cash-out cluster. The graph illustrates that initially the funds were accumulated via transaction with insanely high number of input addresses (merged in thick lines), and then followed those chains of consecutive transfers for obfuscation.

Proceeds withdrawal
Top-10 recipients of the stolen funds
| # | Cluster | Amount |
|---|---|---|
| 1 | Huobi Global | 89146 BTC |
| 2 | WasabiWallet | 25876 BTC |
| 3 | Unknown | 16601 BTC |
| 4 | OKCoin / OKex | 11715 BTC |
| 5 | Unknown | 6051 BTC |
| 6 | Unknown | 4794 BTC |
| 7 | Unknown | 3270 BTC |
| 8 | Unknown | 3264 BTC |
| 9 | Unknown | 3143 BTC |
| 10 | Unknown | 2187 BTC |
Grouped by names:
| # | Cluster | Amount |
|---|---|---|
| 1 | Huobi Global | 89146 BTC |
| 2 | Unknown | 79330 BTC |
| 3 | WasabiWallet | 25876 BTC |
| 4 | OKCoin / OKex | 11715 BTC |
| 5 | FCoin | 476 BTC |
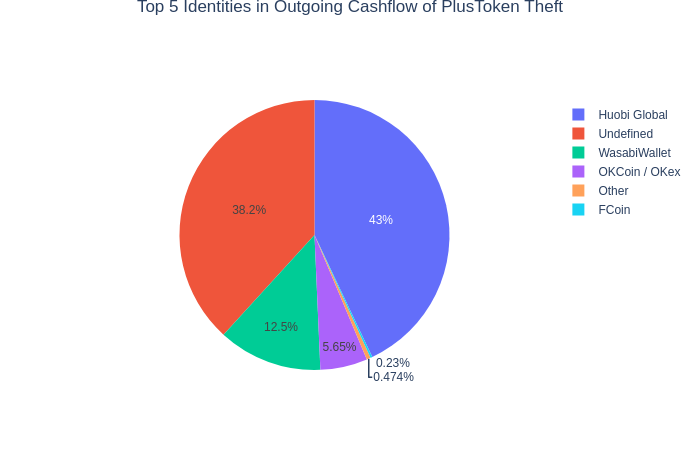
Huobi and OKCoin are the largest recipients among exchanges. Big chuck of the funds refers to unidentified clusters which presumably are linked to exchanges too after few hops. Here is one such example:
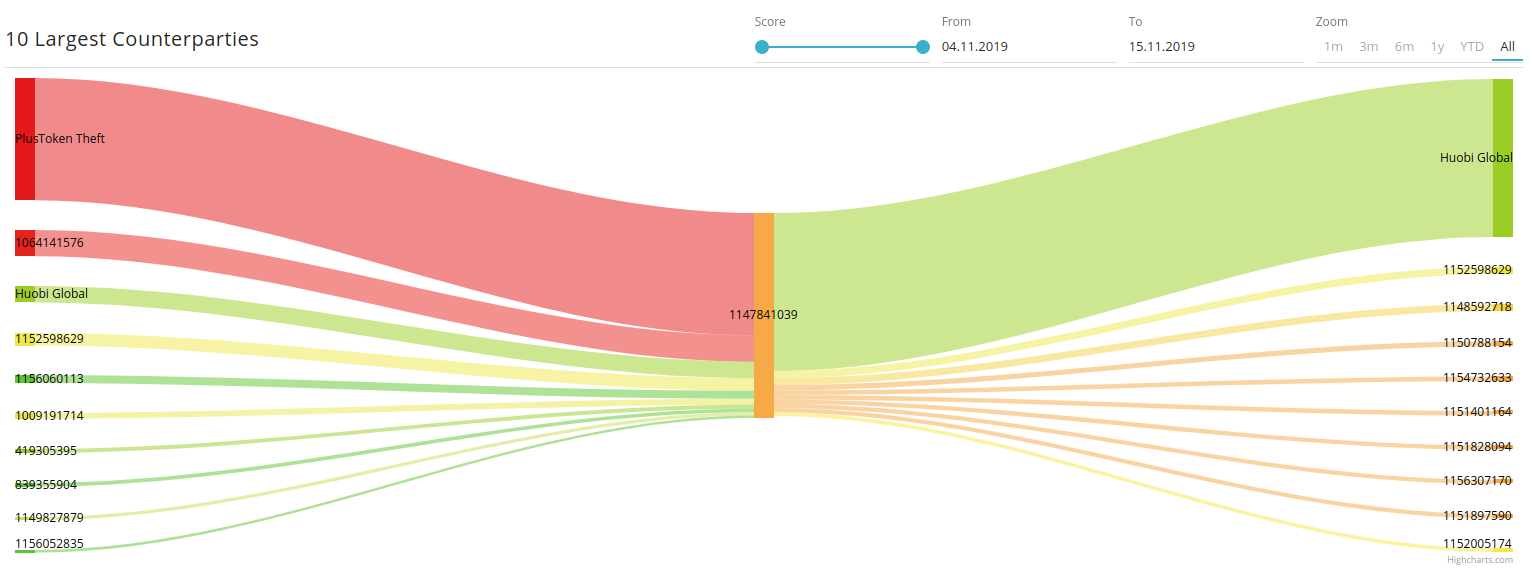
This could be an OTC trader tightly connected with Huobi, but we cannot have an absolute certainly in these cases.
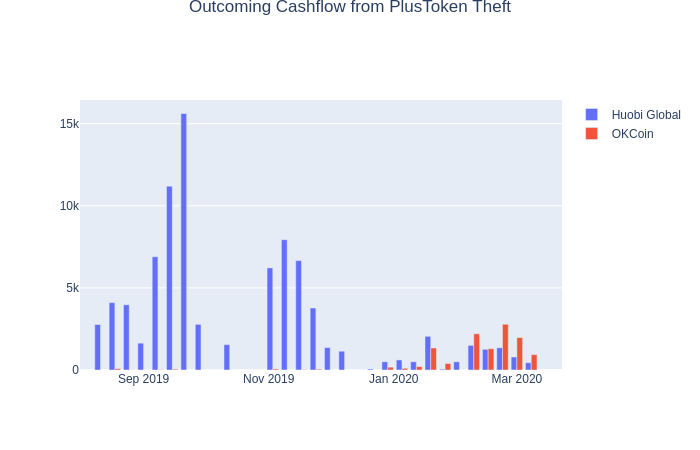
Timewise, the transfers to Huobi and OkCoin exchanges were not simultaneous. The chart of transactions indicates that OkCoin transfers were used at much later period.
Looking at the Huobi addresses the fraudsters used to deposit their funds, you will not find many at all – only around 100. This is a relatively small number given the BTC values accepted. The top-5 addresses eventually ended up with thousands of BTC on the balance and it remains very dubious why this activity was not put on the radar of the exchange.
| # | Address | Amount |
|---|---|---|
| 1 | 1JeyfU5ECq3wNGw1fkSaTSKna4tTvbenVH | 19259.838400 BTC |
| 2 | 1BxVHak5y78VNiYzEWZRAAFiY38E8FmSwp | 17765.637707 BTC |
| 3 | 13uj58xU6fbAp3HJK1DnSbGqDXMCdL6ouH | 10382.432524 BTC |
| 4 | 1Fs6qzvhtvugAXccHTRb3orJqV3mJy3BSk | 6382.000000 BTC |
| 5 | 1KmF5nHDF3z8jdPCQNd9mhfKycxv4iTvHL | 3548.978613 BTC |
We have also noted the dates when these addresses first became active. Surprisingly, some of them date back to 2017 and 2018, implying that these clients should have been well known to the exchange.
| # | Address | First Seen | Last Seen |
|---|---|---|---|
| 1 | 1JeyfU5ECq3wNGw1fkSaTSKna4tTvbenVH | 2017-11-05 14:13:30 | 2020-03-18 11:24:54 |
| 2 | 1BxVHak5y78VNiYzEWZRAAFiY38E8FmSwp | 2018-06-07 17:34:15 | 2020-03-19 10:42:22 |
| 3 | 13uj58xU6fbAp3HJK1DnSbGqDXMCdL6ouH | 2019-09-09 02:53:24 | 2019-11-27 11:21:42 |
| 4 | 1Fs6qzvhtvugAXccHTRb3orJqV3mJy3BSk | 2019-09-03 10:18:21 | 2019-09-23 02:55:56 |
| 5 | 1KmF5nHDF3z8jdPCQNd9mhfKycxv4iTvHL | 2019-08-13 17:55:57 | 2020-03-11 04:19:36 |
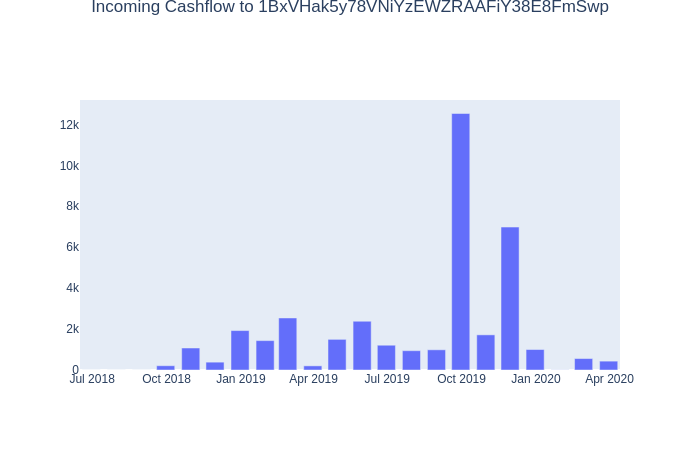
For example, here is the funds flow chart to one such address 1BxVHak5y78VNiYzEWZRAAFiY38E8FmSwp reflecting significant amounts coming since 2018:
WoToken
WoToken is yet another ponzi that actively operated until October 2019.
In the course of our research, it appeared that WoToken was also engaged in PlusToken saga. Similar to PlusToken, it shared the same largest counterparty Huobi, which makes perfect sense as the both schemas have Asian geography.
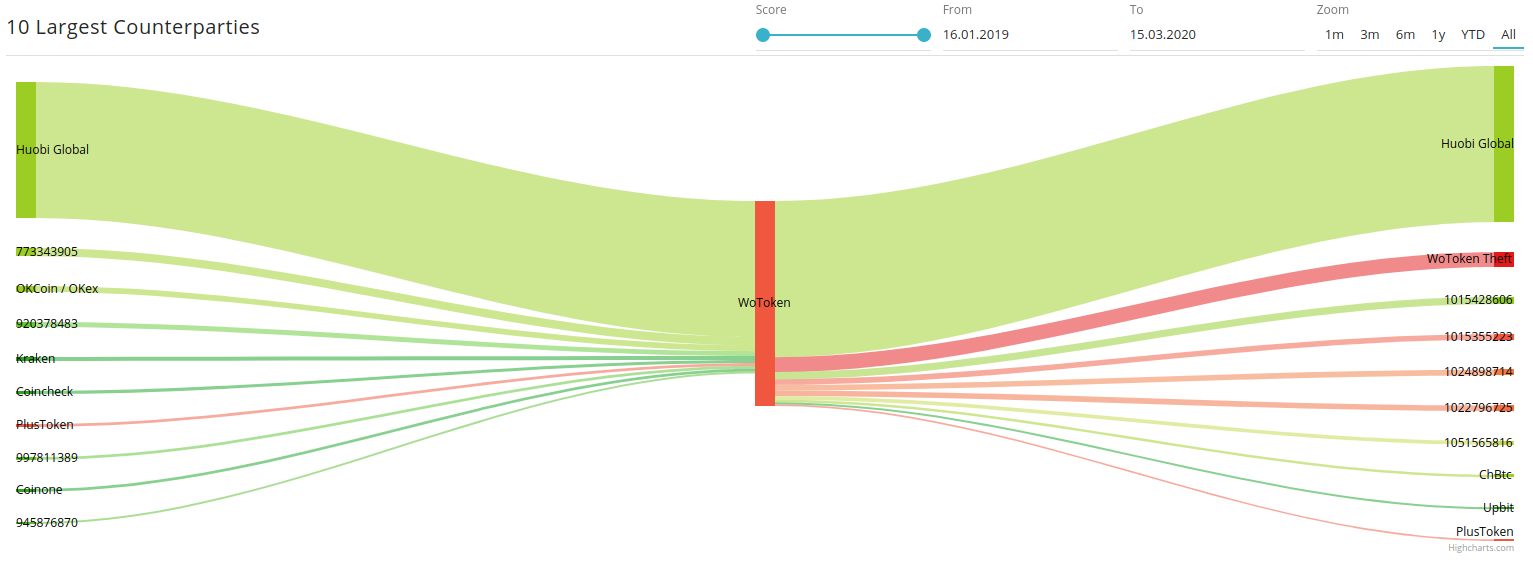
WoToken theft amounted to much less proceeds, i.e. around 4 600 BTC but the flow if this theft headed to those famous CoinJoin-like transactions the PlusToken fraudsters were busy to execute.
We looked at transactions that translated WoToken theft into PlusToken cluster and bring one for the readers’ attention:
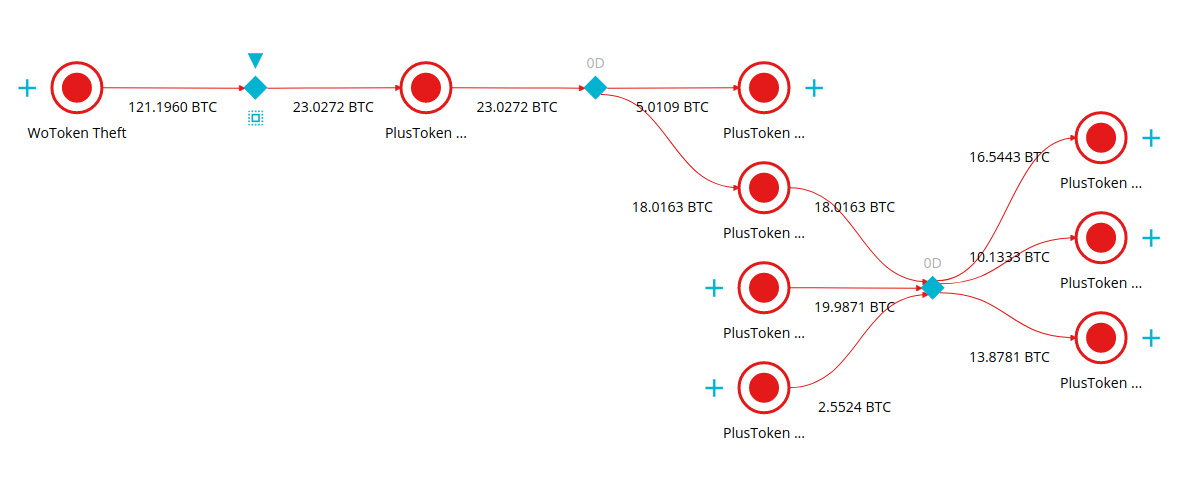
Our thought initially was that CoinJoin-like transactions were mixing inputs that effectively belonged to PlusToken fraudsters. But as it turned out with WoToken analysis, these transactions also involved proceeds from another offense and respectively led us to the following conclusions:
- WasabiWallet is a service that seems to be used only by cyber criminals and the strange thing is that no other parties were involved there at the time of the launder.
- Originators of PlusToken and WoToken are the same entities. The laundering schema does not employ any other participants except those two.
Mixing the proceeds from PlusToken and WoToken does not allow us to effectively distinguish one criminal proceeds from the other. Yet we were able to determine the overall scale of the stolen funds which does not change the whole picture as such.
The analyzed data on plusToken theft is available to all our clients on platform where they can continue to search for the interesting insight and follow developments of other events
Graph visualization was performed using graphistry gpu cloud: https://www.graphistry.com/