2019-06-05
Clain Team
Since the end of December 2018, Electrum a widely used cryptocurrency wallet, has been under severe phishing attacks, which are still ongoing. We have been closely monitoring the situation and we are able to share some of the insight we gained so far.
Using Clain analytics and investigation platform, we were able to trace the flow of the stolen coins. We concluded that the attacks could be roughly grouped into 2 rounds, presumably orchestrated by at least 2 independently acting hackers.
The first round of attacks kicked off before the end of the year. On 27 Dec 2018, the hacker started to aggregate stolen funds on bitcoin address 4MVEf1X4Qmrpxx6oASqzYzJQZUwwG7Fb5, from which he transferred the funds to 1MkM9Q6xo5AHZkLv2sTGLYb3zVreE6wBkj.
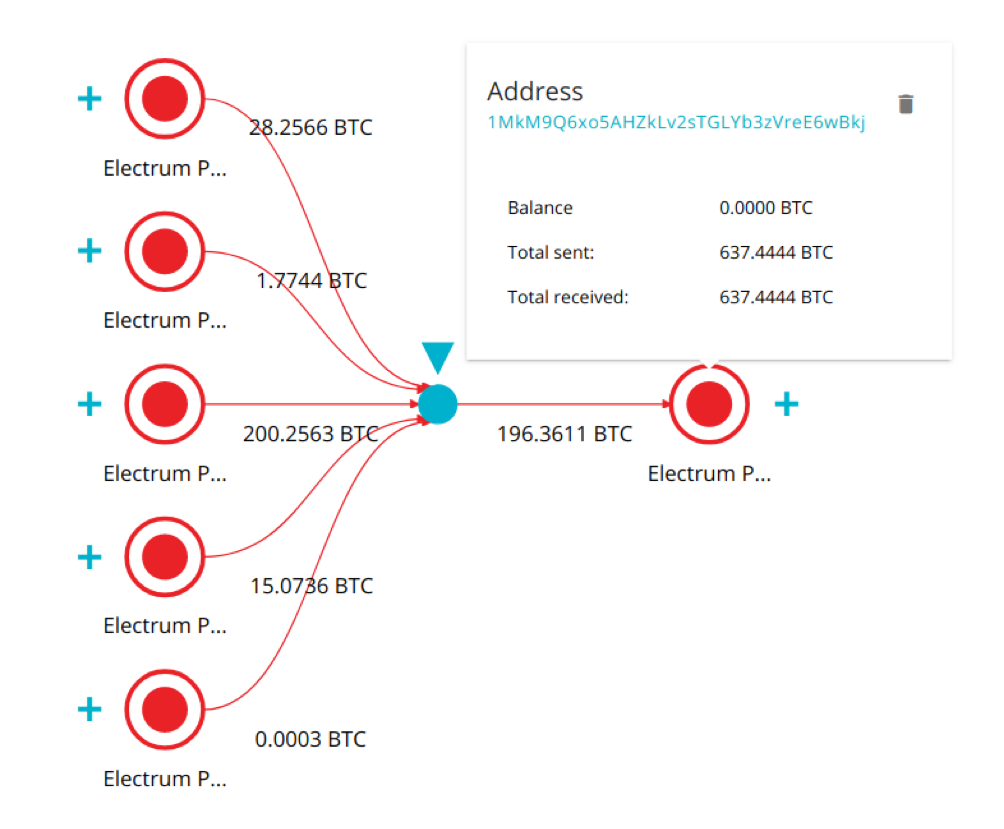
Starting from 19th of January, the BTC funds in small chunks, not to exceed 1 BTC per single transaction, were systematically transferred to MorphToken for exchange into XMR (Monero).
Here is an example of a typical BTC-to-XMR on MorphToken Exchange that a hacker employed.
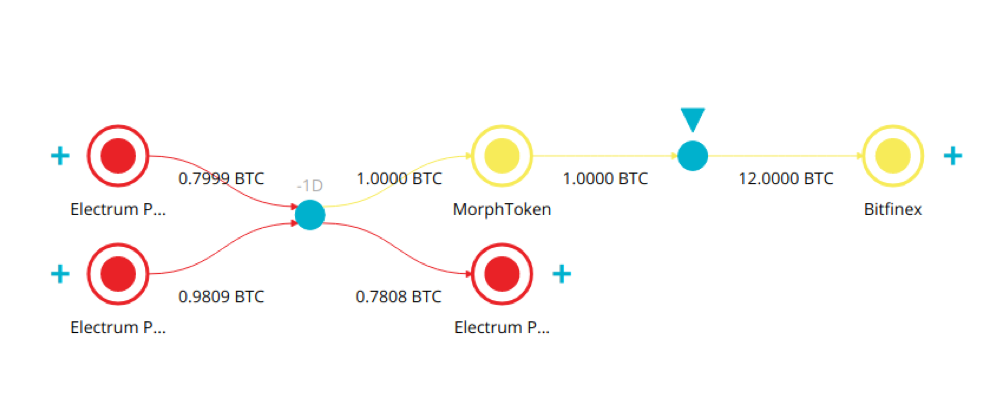
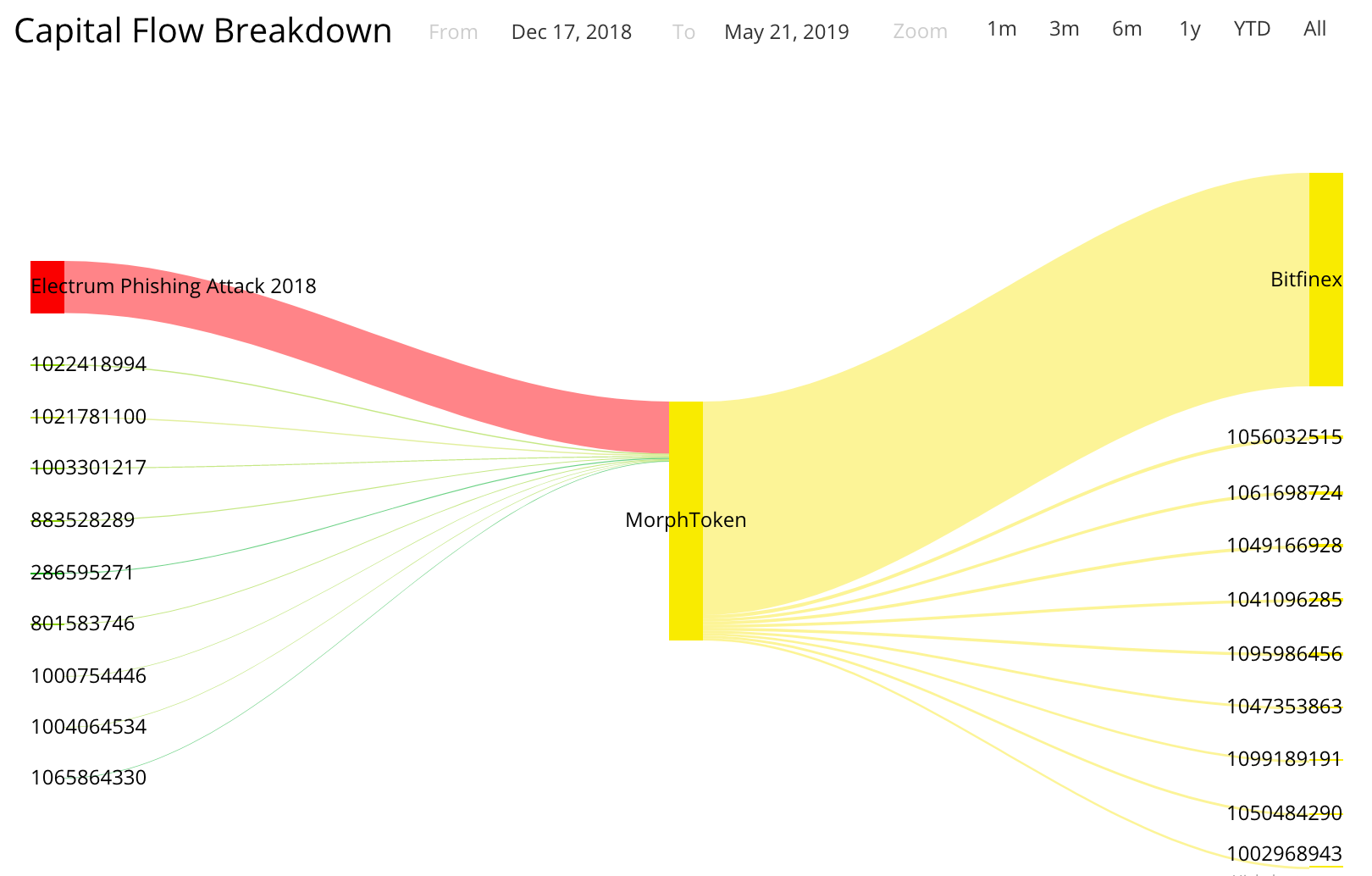
As of 24th of January, a hacker was able to launder 255BTC via MorphToken. The subsequent attacks, taking place between 1st and 6th of February and using the same schema, resulted in additional launder of 176 BTC.
In total, a hacker succeeded in channeling 431 BTC via MorphToken so far.
Important to note though, that MorphToken extensively uses Bitfinex Exchange to manage its crypto exposure; so technically the stolen coins ended up on the books of Bitfinex before being further obscured.
Clain attempted to contact MorphToken for comments with no replies.
The second round of attacks, commenced in February, is still on. We managed to determine that all the funds stolen during this round rushed into Bisq Exchange, again in small chunks equal to 1 BTC excluding commissions.
Below is a sample of the pattern, a hacker followed repeatedly to launder at least 372 BTC by now.
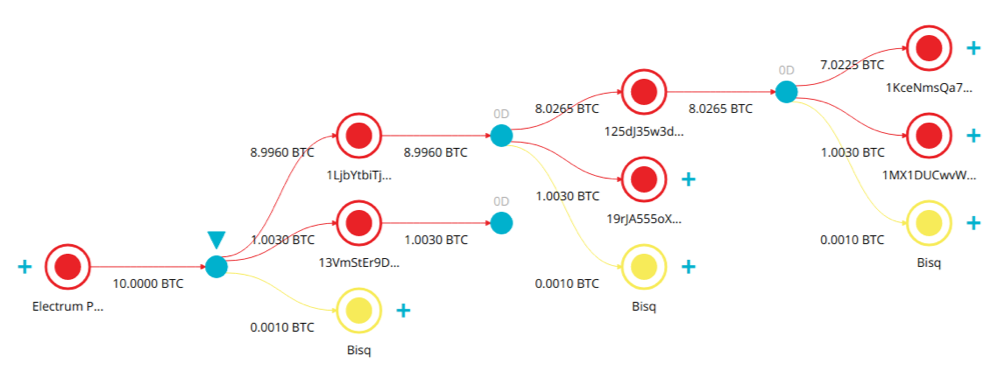
Every transaction consists of three outputs: (1) deposit address, (2) change address, (3) and exchange commission address.
The number of stolen coins using this schema increases with each passing day.
Our analysis of the Electrum attacks for the entire period made us believe there were at least 2 independently acting hackers, whose criminal proceeds were not shared. Each group used its own laundering schema as described above.
In both rounds of attack, hackers enjoyed decentralized nature of exchanges that allowed them to effectively convert criminal proceeds into the currencies of much greater privacy without passing KYC.
We also were left pondering why some of the centrally managed exchanges remained so inactive to the threats of dealing with decentralized counterparties, such as MorphToken.
We use cookies to give you the best possible experience on our website. By continuing to browse this site, you give consent for cookies to be used. For more details, including how you can amend your preferences, please read our Privacy Policy and Cookie Policy
we are happy to talk and will get back to you as soon as possible